
Digital Twin Cybersecurity: Best Practices 2025
Share
Digital twins are transforming how power plants operate, offering real-time monitoring and predictive maintenance capabilities. But with these advancements come serious cybersecurity risks. Hackers can exploit vulnerabilities in sensors, communication channels, and machine learning models to disrupt operations or compromise safety. This article outlines key threats to digital twin systems and practical steps to secure them, focusing on power plants and critical infrastructure.
Key Takeaways:
- Threats: Sensor data manipulation, hyperparameter attacks, remote access exploitation, and integration risks with power grids.
- Solutions: Zero trust access policies, data encryption, anomaly detection, and compliance with standards like NIST IR 8356 and ISA/IEC 62443.
- Governance: Regularly update OT asset inventories, enforce vendor security checks, and secure cloud deployments.
By addressing these risks, power plants can protect their systems while leveraging the benefits of digital twin technology.
Digital Twin Cybersecurity Framework: Threats, Solutions & Compliance for Power Plants
Cyber-Physical Digital Twins for Intrusion Detection
sbb-itb-501186b
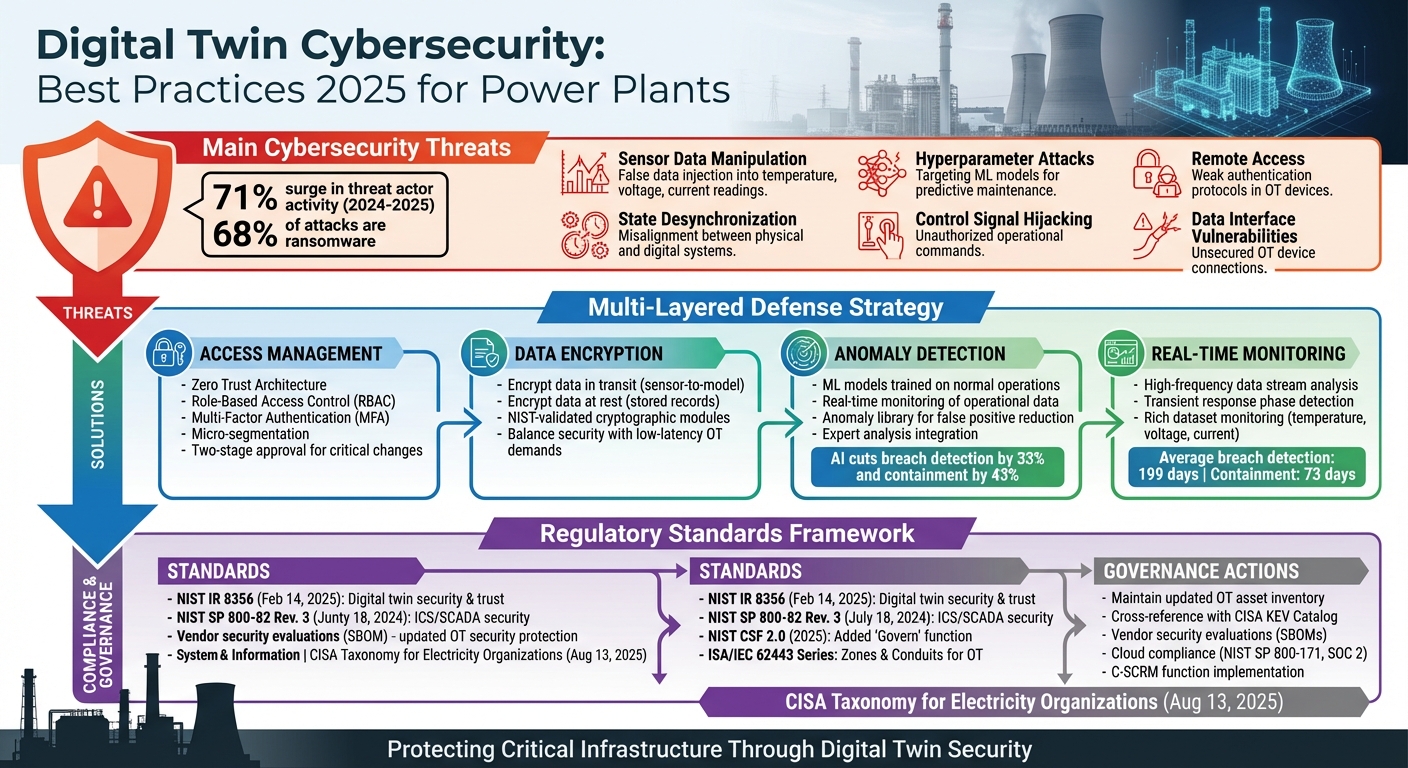
Main Cybersecurity Threats to Digital Twin Systems
Power plants are increasingly vulnerable to cyber threats that specifically target digital twin systems. These threats exploit the way digital twins function - relying on constant data exchange between physical assets and their virtual counterparts. Identifying these risks is essential for protecting digital twin operations and the broader grid infrastructure they connect to. By understanding these challenges, organizations can take the first steps toward building stronger defenses.
Cyber Attacks and Data Breaches
One major concern is sensor data manipulation. Attackers can inject false data into streams like temperature, voltage, or current readings, tricking the digital twin into showing normal operations while the physical system is being compromised. This creates a dangerous blind spot where operators unknowingly act on corrupted information.
In February 2023, researchers from NIST and the University of Michigan demonstrated how this type of attack works. They built a digital twin of a 3D printer and launched controlled cyberattacks, including one that falsified temperature readings. Their machine learning framework was able to distinguish these malicious actions from legitimate anomalies, such as an external cooling fan affecting the printer.
Another threat, hyperparameter attacks, targets the machine learning models used in digital twins for predictive maintenance. By tampering with these parameters, attackers can degrade the accuracy of anomaly detection, making it harder to identify both equipment failures and cyber intrusions. A study conducted by Idaho National Laboratory in September 2023 explored this risk, focusing on digital twins used in advanced nuclear reactor systems. The research, led by Christopher M. Spirito, revealed how vulnerabilities in the interface between digital twins and advanced sensors could be exploited through such attacks.
Remote access exploitation is another pressing issue. Many digital twins rely on real-time operational technology (OT) data, often from devices that lack modern authentication protocols. When these devices are connected to the public internet, they become easy targets for attackers. Cybercriminals frequently use standard internet tools to locate and exploit these weaknesses, particularly in U.S. critical infrastructure.
While these threats are serious on their own, they become even more dangerous when digital twins are integrated with complex external systems.
Integration Risks with Power Grids
The integration of digital twins with power grid infrastructure introduces additional vulnerabilities. The U.S. electric grid is evolving from a relatively isolated system into a highly interconnected network. This evolution expands the attack surface, making digital twins tied to grid operations more susceptible to cyber threats. Each new connection point between a digital twin and grid equipment becomes a potential entryway for malicious actors.
One key risk is state desynchronization, where the alignment between a physical system and its digital twin is disrupted. This misalignment can lead to incorrect diagnostics and poor decision-making. In nuclear facilities, for example, inaccurate safety assessments could have catastrophic consequences.
Control signal hijacking is another significant threat. Digital twins often issue operational commands autonomously, and if compromised, they could execute unauthorized changes to a plant’s physical state. Between 2022 and 2023, a research initiative involving the Nuclear Regulatory Commission, Idaho National Laboratory, and Oak Ridge National Laboratory examined these challenges. The initiative, which included over 75 presenters and 700 global participants, highlighted the regulatory and security risks tied to these systems.
Additionally, data interface vulnerabilities emerge when operational data from OT devices is directly accessed to feed a digital twin. If these connections aren’t properly secured, they can jeopardize the performance and safety of physical processes. These vulnerabilities often stem from standard practices, such as system integrators using default configurations or managed service providers failing to secure interfaces adequately.
These integration risks emphasize the importance of robust security strategies that address not only digital twin operations but also their connections to critical infrastructure.
How to Secure Digital Twins
As digital twins gain prominence, the need to safeguard them becomes critical. With threat actor activity surging by 71% and ransomware accounting for 68% of attacks, a strong, multi-layered security strategy is essential. This approach must address both the virtual models and their connections to physical systems. Below are key strategies to bolster digital twin security.
Access Management and Least-Privilege Policies
Managing access is your first line of defense. A zero trust architecture operates on the principle that no user or device is inherently trustworthy, even within the network. Zac Amos, Features Editor at ReHack, explains:
Zero trust architecture operates on the principle that no user or device should be trusted by default, even if it's inside the network perimeter.
Implement role-based access control (RBAC) to ensure permissions align strictly with job responsibilities. For example, an engineer monitoring turbine performance shouldn't have the same access as a technician maintaining cooling systems. Additionally, enforce multi-factor authentication (MFA) at every login to reduce the risk of compromised credentials.
Micro-segmentation is another essential step. By dividing the network into isolated zones, you can prevent attackers from moving laterally if they breach one area. This is particularly important for separating IT systems, operational technology, and the digital twin environment. For critical changes that impact physical equipment, consider a two-stage approval process - similar to a "two-person rule" - to ensure an additional layer of oversight before executing commands.
Regular access reviews are also crucial. On average, a security breach goes undetected for 199 days, with another 73 days needed for containment. Automated identity lifecycle management tools can immediately revoke access when employees change roles or leave, reducing the risk of "privilege creep", where users accumulate unnecessary permissions over time.
These access controls form a solid foundation, which is further strengthened by encryption to protect data flows.
Data Encryption at Rest and in Transit
Encryption is key to securing the data that flows between physical systems and digital twins. According to NIST IR 8356, published on February 14, 2025, encryption ensures the integrity of "electronic representations of real-world entities and the ability to view the states and transitions between states".
Encrypt data in transit to protect real-time communications, such as sensor-to-model data exchanges and command sequences that impact plant safety. For stored data, use NIST-validated cryptographic modules to secure records at rest.
In operational technology environments, encryption must strike a balance between security and performance. NIST SP 800-82 Rev. 3, updated on July 18, 2024, provides guidelines for applying encryption without disrupting the low-latency demands of physical process control. The goal is to protect data without introducing delays that could interfere with real-time operations.
While encryption safeguards data integrity, real-time monitoring enhances security by identifying potential threats as they arise.
Anomaly Detection and Real-Time Monitoring
Traditional cybersecurity tools often focus on network traffic, overlooking the internal operations of machinery. Michael Pease, a mechanical engineer at NIST, highlights this gap:
Typically, I have observed that manufacturing cybersecurity strategies rely on copies of network traffic that do not always help us see what is occurring inside a piece of machinery or process.
Digital twins provide a more comprehensive view. By using machine learning models trained on normal operating conditions, they can detect subtle deviations in operational data that may signal a cyberattack. Dawn Tilbury, Professor of Mechanical Engineering at the University of Michigan, notes:
Because manufacturing processes produce such rich data sets - temperature, voltage, current - and they are so repetitive, there are opportunities to detect anomalies that stick out, including cyberattacks.
To reduce false positives, build an anomaly library of known, non-malicious issues. When the system flags an irregularity, it can cross-check against this library. Incorporating expert analysis helps refine detection models to identify new anomalies.
AI-driven monitoring has proven effective, cutting breach detection times by 33% and containment times by 43%. Focus on high-frequency data streams and ensure your system can detect attacks during transient response phases - when equipment is shifting between operational setpoints. This blend of automated detection and human expertise creates a dynamic defense capable of adapting to evolving threats.
Compliance and Governance for Digital Twin Security
Regulatory frameworks play a key role in establishing the rules needed to protect digital twin systems. Clear governance ensures that security measures align with established standards without interrupting operations. Together, compliance and governance form a critical part of any cybersecurity plan for digital twin environments.
Regulatory Standards for Power Plants
NIST IR 8356, released on February 14, 2025, is a cornerstone for digital twin security. This report not only addresses traditional cybersecurity challenges but also tackles emerging trust issues unique to digital twins. According to NIST:
Digital twin technology enables the creation of electronic representations of real-world entities and the ability to view the states and transitions between states of these entities.
For operational technology (OT) environments, NIST SP 800-82 Rev. 3 remains the go-to resource. It outlines specific measures for securing industrial control systems (ICS) and SCADA systems, which are often integrated with digital twins. Additionally, the NIST Cybersecurity Framework (CSF) 2.0, updated in late 2025, adds "Govern" as a core function, with new mappings introduced in November 2025 to align with SP 800-53 Rev. 5.
The ISA/IEC 62443 Series offers a practical way to secure OT assets by grouping them into "Zones" with shared security requirements and defining "Conduits" for communication between zones. In early 2025, CISA hosted eight collaborative sessions with 14 organizations, including Duke Energy Corporation, Pacific Gas & Electric Company (PG&E), and Southern California Edison. These efforts led to the "Taxonomy for Electricity Organizations", published on August 13, 2025. This taxonomy provides a standardized framework for classifying OT assets in distribution environments.
To meet CISA's Cybersecurity Performance Goals (CPGs), power plants should maintain an updated OT asset inventory, categorized by function and criticality. CISA underscores the importance of this step:
An OT asset inventory - an organized, regularly updated list of an organization's OT systems, hardware, and software - is foundational to designing a modern defensible architecture.
Cross-referencing your asset inventory with CISA's Known Exploited Vulnerabilities (KEV) Catalog and MITRE's CVE database can help prioritize patches. Implementing the ISA/IEC 62443 standard allows you to segment digital twin assets into zones and monitor the conduits connecting them.
In addition to adhering to formal standards, addressing risks in the external supply chain is equally important.
Vendor and Cloud Governance
Securing digital twins also means managing vendor relationships and cloud deployments effectively. Third-party integrations can introduce supply chain vulnerabilities, making oversight essential. Establishing a Cybersecurity Supply Chain Risk Management (C-SCRM) function can help mitigate risks across both ICT and OT supply chains.
Leverage resources like NIST SP 800-161r1 and SP 1326 to evaluate vendor security claims, ensuring providers deliver regular vulnerability updates and Software Bill of Materials (SBOMs). For cloud-based digital twins, confirm that providers comply with NIST SP 800-171 and SOC 2 standards to safeguard sensitive engineering and operational data.
For power plants, digital twin governance must align with NIST SP 800-82 Rev. 3 to meet the specific performance, reliability, and safety demands of operational technology.
Beyond traditional security measures, it’s crucial to evaluate the “trust” factor in digital twins - how accurately the digital representation mirrors the state of the physical system. This concept, outlined in NIST IR 8356, ensures the integrity of the data exchanged between physical and virtual systems.
Strong governance and thorough supply chain management are the backbone of any effective strategy for securing digital twins.
Conclusion
The cybersecurity measures we've discussed are not just technical necessities - they are the backbone of maintaining operational integrity in power plants. Securing digital twin systems is crucial to ensuring safe and efficient operations as we approach 2025. The bidirectional data flow in these systems - where information moves from the physical plant to the digital twin and control signals return - introduces unique vulnerabilities that require tailored protection strategies. Without strong defenses, the very features that make digital twins valuable could also become pathways for cyberattacks.
Cybersecurity plays a key role in enabling predictive maintenance, reducing costs, and ensuring reliable synchronization between physical systems and their digital counterparts, particularly in nuclear power generation.
Strategies like network segmentation, least-privilege access, encryption, and real-time anomaly detection are essential for minimizing breach impacts and preventing attackers from moving freely within systems. The Cybersecurity and Infrastructure Security Agency (CISA) underscores the importance of fallback measures:
The capability for organizations to revert to manual controls to quickly restore operations is vital in the immediate aftermath of an incident.
The urgency of these measures is underscored by the rising threat landscape. Between 2024 and early 2025, threat actor activity surged by 71%, with ransomware accounting for 68% of cyberattacks. To counter these threats, power plants must prioritize digital twin security by eliminating public exposure of operational technology, implementing phishing-resistant multi-factor authentication, and keeping asset inventories up to date. These steps not only mitigate risks but also ensure that digital twins can operate at their full potential.
With effective cybersecurity in place, power plants can trust their data, validate control signals, and maintain safe operations. By following the practices outlined here and aligning with frameworks like NIST IR 8356, power plants can protect their critical infrastructure while fully leveraging the benefits of digital twin technology.
FAQs
What are the top cybersecurity risks for digital twin systems in power plants?
Digital twin systems in power plants face a range of cybersecurity challenges that demand attention. Unauthorized access to digital twin data or models can result in tampering or misuse of sensitive information, potentially jeopardizing operations. Threats like malware and ransomware attacks can compromise system integrity, leading to operational disruptions or financial setbacks. A lack of proper network segmentation further increases vulnerability by expanding the attack surface. Moreover, supply chain weaknesses and insider threats add another layer of complexity, often making breaches harder to detect.
To address these risks, it's crucial to implement strong security measures. This includes enforcing strict access controls, ensuring systems are updated regularly, and maintaining continuous monitoring to safeguard critical infrastructure effectively.
What are the best practices for implementing zero-trust access policies in digital twin systems for power plants?
To put zero-trust access policies into action for digital twin systems in power plants, start by assuming that every user, device, and service is untrusted until verified. Begin with a detailed inventory of all digital twin assets - like simulation servers, data historians, and sensor feeds. Once you’ve mapped these out, group them into logical trust zones, such as IT, DMZ, and OT, and define clear boundaries for each. Always validate the status of each asset before granting access, ensuring no blind spots in security.
Strengthen your identity and access controls by implementing multi-factor authentication (MFA) and applying role-based or attribute-based access policies. This ensures users only get the minimum level of access they need to perform their tasks. For device-to-device communication, secure it with certificates or mutual TLS, and make sure every interaction with the twin model is authenticated and logged.
To further tighten security, leverage network segmentation techniques like micro-segmentation and secure gateways. These measures help contain potential breaches, preventing them from spreading across different zones. Continuous monitoring and anomaly detection are crucial here - combine these with automated policy enforcement to quickly identify and respond to threats in real time. Tools such as hardened firewalls and secure switches, available through Electrical Trader, can simplify the process of building a strong zero-trust architecture while enhancing security.
What security standards should power plants follow to protect digital twin systems?
To strengthen the security of digital twin systems, power plants should adhere to key recommendations from the National Institute of Standards and Technology (NIST). These include:
- Security and Trust Considerations for Digital Twin Technology (IR 8356, 2025)
- Guide to Operational Technology (OT) Security (SP 800-82 Rev. 3)
- Cybersecurity Framework (CSF 2.0)
- Smart Grid Cybersecurity Guidelines (IR 7628)
These guidelines outline strategies to protect critical infrastructure, address potential vulnerabilities, and align with best practices in the industry.
